In today’s business landscape, email security has become a top priority. In 2022 alone, over 48% of emails that were sent across the internet were spam. With the continuing rise of cyber threats related to emails, it’s essential now more than ever to protect your communication.
As we navigate the digital realm, understanding the importance of email security and the prevalence of email-related cyber threats is the first step to safeguarding your business communication. Now, let’s explore simple and actionable strategies that will empower you to navigate the digital world securely and safely.
Strong Passwords
Strong passwords act as the first line of defense against unauthorized access to your inbox, making it essential to understand their importance. A robust, unique password significantly reduces the risk of cyberattacks and data breaches.
To create and manage secure passwords, consider employing a combination of upper and lower-case letters, numbers, and special characters. Avoid common and easily guessable phrases or patterns. Password management tools like LastPass can also simplify the process by generating and storing complex passwords securely in an encrypted vault. By prioritizing strong, unique passwords, you’re not only protecting your sensitive business information but also bolstering the overall security of your email communications.
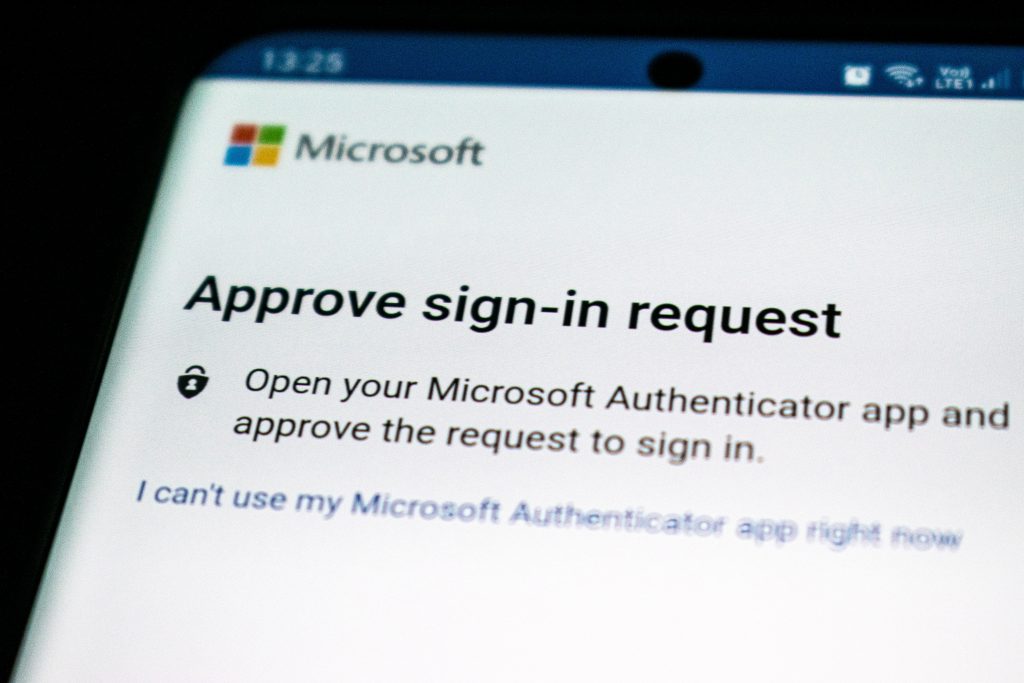
Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) is your email security’s best friend. It acts like an extra layer of defense, making sure your email account is like a fortress. Setting up 2FA is usually a breeze, and it’s done right in your email settings.
Essentially, it’s all about linking your email to another device, such as your smartphone. Then, when you log in, you’ll get a one-time code to prove it’s really you, often sent via text or email. This extra step makes it much more difficult for anyone else to sneak into your email. Popular email providers like Google and Microsoft each provide their own guides on setting up two-factor authentication. So, if you’re a business pro and you want to keep your sensitive messages and data safe, 2FA is a no-brainer. Essentially, it’s like having a reliable bodyguard for your inbox.
Beware of Phishing Emails
Vigilance against phishing emails is paramount for business professionals. Phishing emails are cleverly disguised as legitimate communications but harbor ill-intentions. They typically lure recipients into revealing sensitive information, clicking malicious links, or downloading harmful attachments. Recognizing these fraudulent emails is the first line of defense, and thankfully sources like the Federal Trade Commission (FTC) offer helpful tips on spotting phishing scams.
Be wary of unsolicited requests for personal or financial data, grammatical errors in the message, and generic greetings. Legitimate organizations rarely ask for sensitive details via email. Hover over links to preview the URL before clicking, and scrutinize sender addresses. It’s crucial to stay informed and educate yourself and your team on these telltale signs to ensure you never fall victim to these deceptive tactics, safeguarding both your business and your reputation.
Keep Software Updated
Software updates are more than just feature enhancements; they often include critical security patches that shield your email communication from vulnerabilities. These updates act as safeguards against emerging threats and ensure that your email client or app remains resilient to potential attacks.
It’s crucial to establish a routine for checking and applying updates. Most email clients and applications offer automatic update settings, making the process effortless. By regularly updating your software, you’re not only optimizing your email experience but also fortifying the digital walls around your sensitive data and communications. In an era of ever-evolving cyber threats, staying current is a potent shield against potential security breaches.
Use Secure Networks
In the age of remote work and on-the-go business operations, using secure networks for your email communication is a critical practice that every business professional should embrace. Unsecured Wi-Fi networks pose inherent risks to your data security, as they are often prime hunting grounds for cybercriminals seeking to intercept sensitive information.
To protect your email exchanges, it’s vital to exercise caution when using public networks, especially in coffee shops, airports, or hotels. Shield your email communications by connecting to virtual private networks (VPNs) that encrypt your data, rendering it unreadable to prying eyes. For those concerned about the priciness of a VPN, consider utilizing a budget-friendly option like ExpressVPN or Surfshark, Additionally, ensure that your email client or app uses secure connections (SSL/TLS) to encrypt your email traffic. By adopting these precautionary measures, you’re fortifying your email security, ensuring that your vital business communications remain confidential and protected, even when you’re working on the move.
Email Encryption
Email encryption is the digital cloak of confidentiality that every business professional should be well-versed in. This security practice involves encoding your email messages, making them unreadable to anyone except the intended recipient. In a world where data privacy is paramount, email encryption ensures that your sensitive business information remains classified.
There are various tools and methods available to achieve this security feat, like Proton Mail. Some email clients offer built-in encryption features, simplifying the process. Alternatively, third-party encryption services and plugins can be integrated with your email platform. The choice of tool often depends on your specific needs and preferences. By embracing email encryption, you’re not only safeguarding your confidential communications but also demonstrating your commitment to data protection and integrity, a quality highly regarded in the business world.
Regular Backups
The importance of email backups cannot be overstated, as they act as a fail-safe mechanism in case of unforeseen data loss, whether due to hardware failures or cyber incidents. Setting up and maintaining email backups is a straightforward yet essential practice.
Most email clients and servers offer automatic backup options that allow you to archive your email history. It’s prudent to set up scheduled backups, ensuring that your critical data is continuously preserved. Regularly check the integrity of your backups and confirm that the restoration process works seamlessly. By embracing this practice, you not only protect your business from potential data disasters but also uphold a level of professionalism that is highly regarded in the world of business. Your commitment to data preservation and continuity sets you on a path of email security and reliability that is indispensable in today’s digital landscape.
Employee Training
Your team’s awareness and actions play a pivotal role in defending against email threats. The first step is to acknowledge that the human element is often the weakest link in email security, and training can bolster this vulnerability.
By fostering a culture of vigilance and imparting knowledge about the various email threats that exist, you empower your staff to recognize and respond to suspicious emails effectively. This can include conducting simulated phishing exercises, providing guidelines for email etiquette, and offering regular updates on the latest threats and best practices. With a well-informed and alert team, you not only reduce the risk of breaches but also create a resilient email security environment that aligns seamlessly with your business’s goals and values.
Spam Filters
Spam filters are the unsung heroes of your email inbox, silently working behind the scenes to protect you from a barrage of unsolicited and potentially harmful emails. Understanding how these filters function is crucial for business professionals aiming to maintain a clutter-free and secure email environment. Spam filters operate on algorithms that scan incoming emails for specific markers commonly associated with spam, such as dubious sender addresses, certain keywords, or unusual attachment types.
While most email clients come with default spam filters, it’s beneficial to customize these settings to align with your specific preferences. By adjusting filter sensitivity, whitelisting trusted senders, and fine-tuning the criteria for filtering, you can strike a balance between a streamlined inbox and ensuring that no legitimate messages are mistakenly marked as spam. A well-configured spam filter keeps your email communication efficient, ensuring that your important business correspondence remains at the forefront while unwanted clutter is relegated to the background.
Report Suspicious Emails
Recognizing the significance of promptly reporting such emails goes beyond personal security—it plays a pivotal role in collective cybersecurity. By reporting suspicious emails, you actively contribute to the broader effort of identifying and neutralizing potential threats, making the digital landscape safer for all.
Most email clients offer user-friendly reporting features, often just a click away. Cooperation in this regard ensures that email filters and security systems continually evolve to counter new and evolving threats. It’s a collaborative effort where business professionals become the frontline defenders, securing their own communications while bolstering the defenses of their peers.
Conclusion
These ten email security tips collectively create a robust shield for your business communication. From strong passwords to reporting suspicious emails, each practice plays a vital role in ensuring your inbox’s security. We encourage fellow business professionals to take action and implement these strategies diligently to safeguard sensitive data and maintain the integrity of their communications. By doing so, you not only strengthen your defenses but contribute to the broader landscape of digital security.